101 | Add to Reading ListSource URL: vast.uccs.eduLanguage: English - Date: 2013-12-13 11:59:39
|
|---|
102 | Add to Reading ListSource URL: cacr.uwaterloo.caLanguage: English - Date: 2011-07-10 02:35:14
|
|---|
103 | Add to Reading ListSource URL: www.vacancylab.comLanguage: English - Date: 2015-12-18 09:30:09
|
|---|
104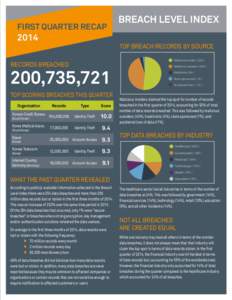 | Add to Reading ListSource URL: breachlevelindex.comLanguage: English - Date: 2016-08-03 15:31:24
|
|---|
105 | Add to Reading ListSource URL: conferences2.sigcomm.orgLanguage: English - Date: 2014-12-01 16:56:14
|
|---|
106 | Add to Reading ListSource URL: www.aclu.orgLanguage: English - Date: 2015-04-10 18:25:21
|
|---|
107 | Add to Reading ListSource URL: tom.vgLanguage: English - Date: 2016-08-03 21:35:58
|
|---|
108![CP-G10i-Flyer-v10.fh-2 [Converted] CP-G10i-Flyer-v10.fh-2 [Converted]](https://www.pdfsearch.io/img/3e74be41646eb1b832b1dfeb40da0938.jpg) | Add to Reading ListSource URL: www.cryptophone.deLanguage: English - Date: 2011-02-28 18:04:53
|
|---|
109 | Add to Reading ListSource URL: epic.orgLanguage: English - Date: 2016-05-25 12:49:19
|
|---|
110 | Add to Reading ListSource URL: essentials.code42.comLanguage: English - Date: 2016-07-16 06:38:47
|
|---|